The Department of Homeland Security (DHS) has described critical infrastructure as the physical assets and cyber systems that are so vital that their incapacity or destruction would have a debilitating impact on the economic security, public health or safety of our nation.
In support of this mission, DHS formed the Cybersecurity and Infrastructure Security Agency (CISA) to be the nation’s risk advisor, working with partners to defend against today’s threats and collaborating to build more secure and resilient infrastructure for the future.
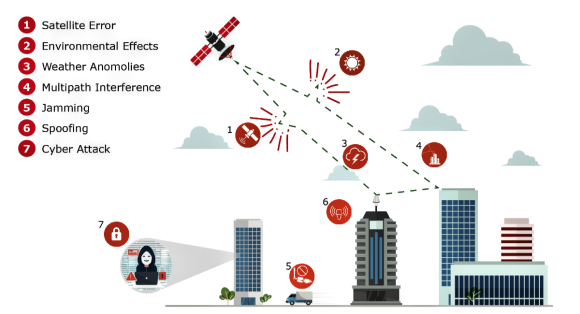 Figure 1: GNSS vulnerabilities can be intentional or unintentional.
Figure 1: GNSS vulnerabilities can be intentional or unintentional.
According to CISA, there is dramatic growth in the degree to which critical infrastructure depends on Global Positioning System (GPS)/Global Navigation Satellite Systems (GNSS) (GPS/GNSS) for the dissemination of “time.” While the use of GNSS-based time has become more vital for critical infrastructure operations, the security of the GNSS signal itself has become increasingly vulnerable to a wide range of jamming and spoofing threats, both intentional and unintentional.
Given the inherently fragile nature of the GNSS signal, an important way in which reception of the GNSS signal can be guarded is through better visibility of the GNSS signal characteristics in real-time, including performing test and measurement of GNSS signals and identifying anomalies. While this work was previously done in the lab and problem diagnosis required substantial GNSS expertise, the latest performance monitoring software solutions create a simple way for operators to know the overall health of GNSS reception.
The World’s de Facto Time Standard
According to CISA, GPS has become the de facto time standard for many commercial users because of its relatively low cost and ubiquitous availability. There also is growing adoption of GNSS devices such as those using GPS. Until recently, GPS devices were viewed simply as radio receivers. These devices are, however, really computers, with similar security risks.
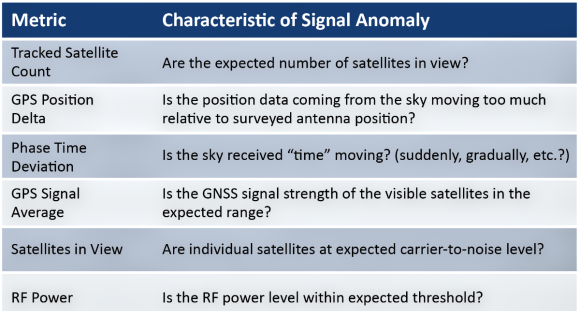 Table 1. Typical characteristics of a GNSS signal.
Table 1. Typical characteristics of a GNSS signal.
Threats include denial-of-service attacks (jamming) and the introduction of bad data into the system (spoofing). The advent of software-defined radios (SDRs) has increased the ease and lowered the cost with which these types of attacks can be launched. Efforts should be made to ensure accurate and resilient timing for your GPS devices.
GNSS signals are inherently fragile. Disruptions are typically classified into two categories: “jamming” that renders the GNSS signal undetectable by overpowering it with a locally generated signal at the same frequency, and spoofing, in which a false GNSS signal is created that the receiver is fooled into tracking. Contained within the fake signal is inaccurate information, such as false location data.
The GNSS signal is very weak and is largely only detected with a clear view of the sky. Given the significant distance the signal must travel from satellites orbiting 12,500+ miles above the earth’s surface, the GNSS signals are at a very low power level (typically –133 dBm) when reaching the Earth’s surface.
Reports of large geographical areas being jammed are now common throughout the world. Further, intentional threats are not the only vulnerability category to be concerned with (see Figure 1. Click on any graphic to enlarge). Errors due to weather, atmosphere and even the operation of the GNSS satellite control system can impact the secure reception of GNSS. This has occurred at a global level for both GPS in 2016 and, more recently, with Galileo unavailability, which just occurred in 2019.
From Surveillance to Characterization
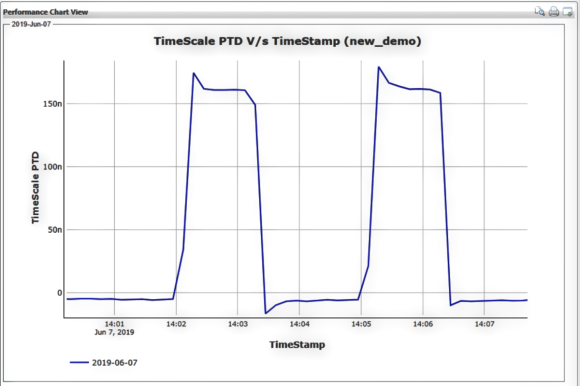 Figure 3. Timing Anomaly — repeating offset of 150 ns.
Figure 3. Timing Anomaly — repeating offset of 150 ns.
GNSS surveillance is the first step, giving network operators the bird’s eye view they need to survey their critical infrastructure. When an anomaly or outage occurs, the most immediate need is to quickly identify if the event is isolated to a specific location, affecting a regional area, or caused by a global situation. If it is a single location being impacted, then the cause can most likely be narrowed down to an issue such as multi-path interference, local weather anomaly or a potential drive-by jamming/spoofing threat (a common example being a vehicle with jamming device).
If the impact is affecting multiple locations, then a more complex problem is likely occurring and narrowing the root cause is more difficult, especially in such cases as the GPS 2016 anomaly and more recent Galileo 2019 outage.
Once the scope of the problem has been pinpointed, the next step is to dig into more of the details. This requires more specific signal characterization to identify root cause.
GNSS simulators typically have highly sophisticated recording capabilities which developers of GNSS receivers and related equipment have been using for years to perform test and measurement of GNSS signals. Such equipment is effective for laboratory environments or even in manufacturing; however, this instrumentation is expensive and requires instrumentation specialists with extensive training. Software is now available that enables network operators to simplify these important measurement and diagnosis capabilities. An example is Microchip’s TimePictra® with its BlueSky Performance Monitoring capabilities. Table 1 to the upper right provides a sample of some of the metrics and signal characteristics that can be tracked with it.
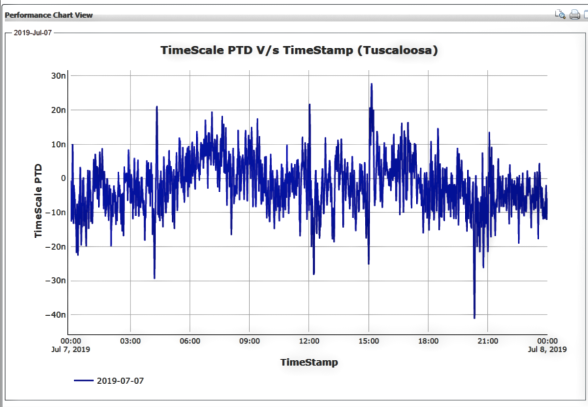 Figure 2. Phase measurements of GNSS reception
Figure 2. Phase measurements of GNSS reception
Visibility of Timing Anomalies
Although GNSS systems are mostly known for “navigation,” the fundamental operation of GNSS is completely dependent on timing accuracy. When determining if the GNSS reception is performing well, measurement of the phase difference between what is expected versus what is being received is a good signal characteristic to visualize (see Figure 2).
Under normal conditions, the phase offset should typically be in the ±50 ns range as seen in the previous plot. Given this small range of acceptable performance, detection of a timing anomaly can be quite difficult and is one of the most important techniques for protecting against GNSS vulnerabilities.
Timing anomalies can be gradual, sudden, or complex such as repeated phase jumps. Timing errors can cause serious havoc and confusion as such errors can cascade down to the underlying timing distribution systems operating a large data center or mobile switching office.
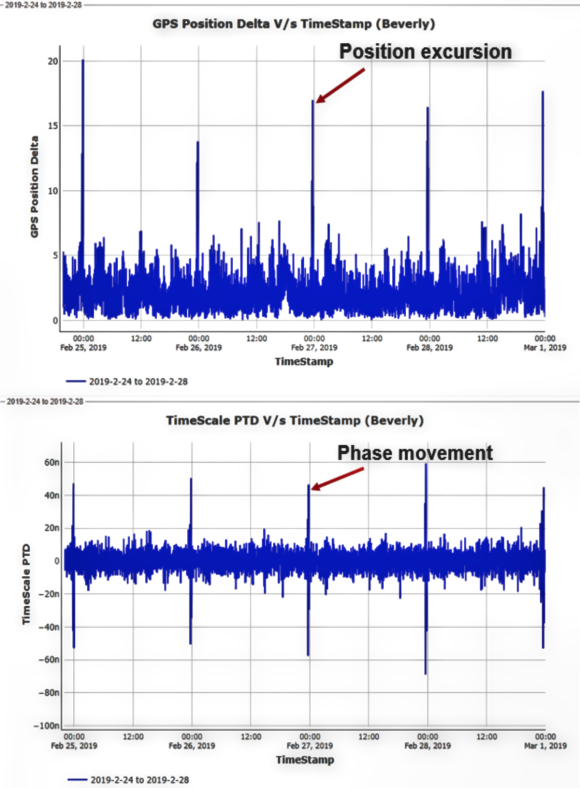 Figure 4. Position excursion creating phase jumps.
Figure 4. Position excursion creating phase jumps.
Below is an example of a timing anomaly where there is a repeated timing offset of roughly 150 ns being generated (see Figure 3). With this type of repeated event, a typical GNSS receiver/timing system could be jumping in and out of holdover causing major confusion for critical infrastructure operation.
Visibility of Position Anomalies
For critical infrastructure, the GNSS antenna is typically installed in a fixed location with a clear view of the sky and the exact position of the antenna is surveyed with the coordinates programmed into the receiver. When the GNSS receiver is being used for “timing,” precise survey of the antenna is necessary to ensure the most accurate timing performance. Any kind of offset and/or spoofed position data can cause the GNSS receiver to have degraded timing performance and ultimately cause the GNSS receiver to lose the ability to track satellites completely.
In the example show in the column to the right, under normal conditions, the position as received by the GNSS receiver is roughly 1 to 5 meters, as compared to the surveyed position of the GNSS antenna.
The first plot in Figure 4 to the upper right shows normal position fluctuation; however, occurring once per day, there is also a position excursion of about 15 to 20 meters. The plot below it is of phase movement which shows a phase shift of roughly 100 ns (peak-to-peak) simultaneous with the position movement of the first plot.
The position movement, which is likely the result of multi-path interference, is impacting timing performance. Multiple GNSS signal characteristics are viewed together so that network operators can better understand cause and effect.
Visibility of Spoofing
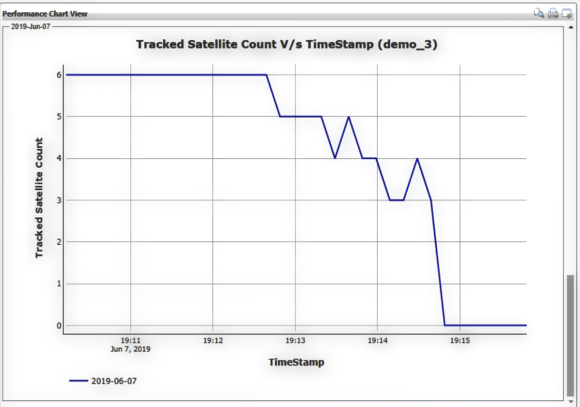 Figure 5. Spoofing of GNSS satellite tracking
Figure 5. Spoofing of GNSS satellite tracking
Spoofing attacks can be difficult to detect as it is the GNSS data itself that is being manipulated. Like data network threats, GNSS spoofing is an on-going and evolving threat vector which requires a defense system that can be upgraded to guard against emerging threats.
As shown in Figure 5 on the next page, a GNSS receiver is tracking six satellites under normal conditions and then satellites begin to be prematurely knocked out. Over the course of approximately three minutes, all satellites are no longer being tracked. Satellites falling out of view this quickly is abnormal and is just a simple example of how spoofing can create a confusing situation for a GNSS receiver trying to track satellites.
Protecting Every Device
Security has become the most important requirement for critical infrastructure operations. Any device connected to critical infrastructure can become a target for exploitation and needs to be as secure as possible.
Security hardening of a GNSS system is a continual process, due to the constant emergence of new threats. Like network security vulnerabilities, new GNSS vulnerabilities are on the rise and GNSS signal visibility is a vital capability for helping to determine the root cause of a GNSS vulnerability, especially before a minor disruption becomes a more serious outage.
When a GNSS vulnerability is detected, today’s performance monitoring software provides surveillance of GNSS reception quality without having to send network operations personnel on an expensive visit to check an antenna on a high-rise rooftop. It enables critical infrastructure operators to quickly identify if the problem is specific to a location or affecting a larger geographical area. It also enables the next step in the mitigation process, giving operators the key performance metrics that are required so they have the visibility to take quick and cost-effective action.
www.microchip.com

Greg Wolff has worked in the time and frequency industry since 1988 and was an early pioneer in the marketing of network synchronization solutions to major critical infrastructure operators across the globe. Greg is an active contributor to emerging standards supporting PNT (Position Navigation and Time) resiliency and most recently, as part of Microchip Technology’s Frequency and Time Systems group, he launched the BlueSky GNSS Firewall.